Restricted Access List

Identify people that are on watchlists
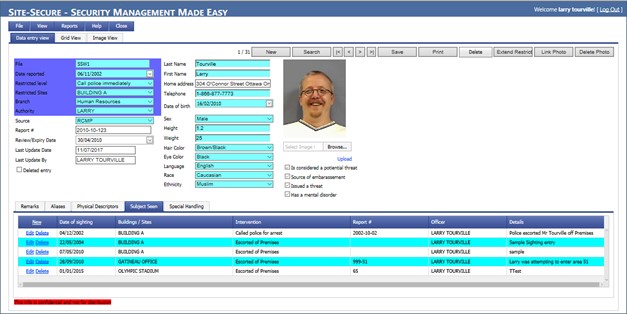
The restricted access person module is particularly effective in screening the access of visitors, contractors or employees in your facilities. When authorized people place restrictions upon individuals, information is usually kept confidential until they try to gain access to the facility. When a person’s name is entered into the system, the user will be prompted if a restriction has been applied to the individual. The severity of the restriction and details on how to process the person can easily be viewed.
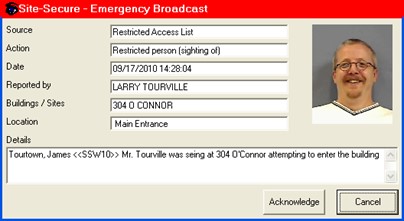
Send an emergency broadcast message with a warning and description of the person
All names entered into the database are saved for several years or until deleted. This module contains the names and, if available, images and aliases, of all individuals with any form of restriction. Administration can view the source and detail of the restriction. You can flag the number of days that a restriction has been imposed to ensure compliance with any law or internal policy. If a restricted person or group of people are attempting to gain entry to your facility through one of a number of access points, it is possible to send an Emergency Broadcast with a warning and complete descriptions.

Automatic email notifications, as part of emergency broadcast (BOLO) messages, can be configured.
Magnifying glass (search)
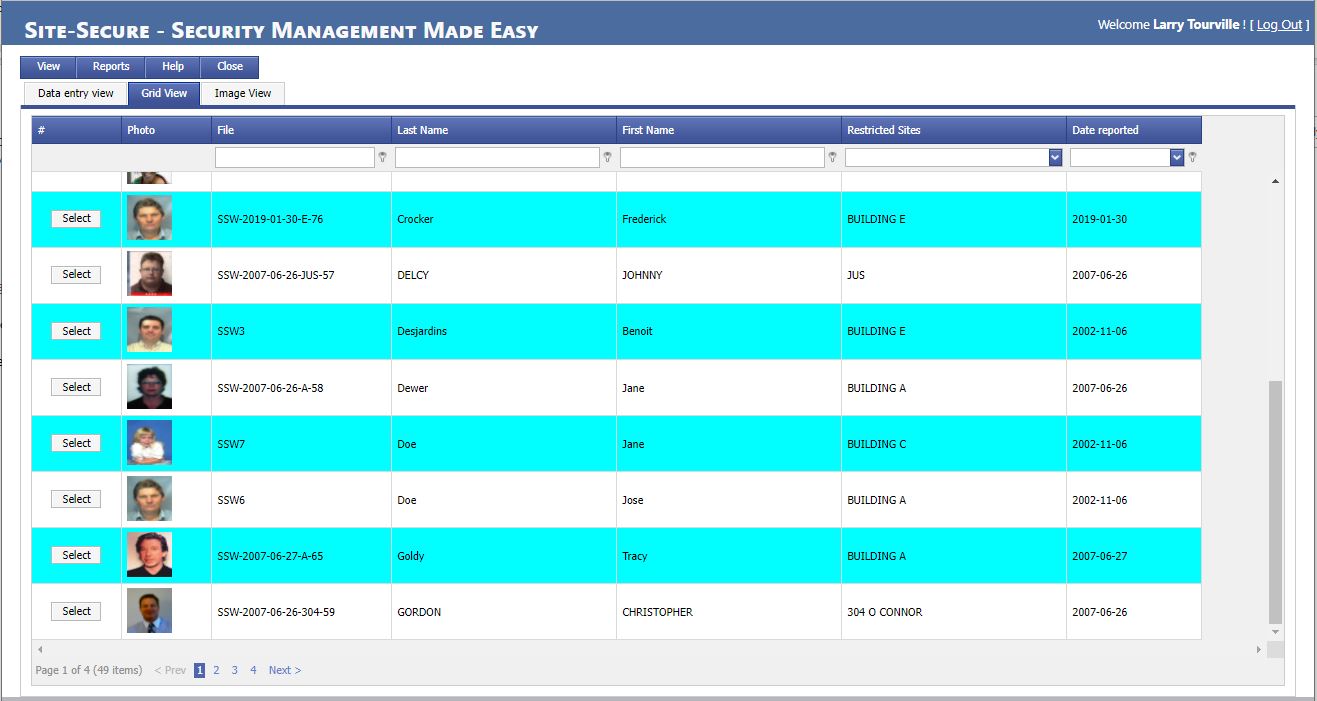
Carry out searches of visitors, contractors and employee in each database.
Integrations
Direct integration with personnel information management, contractors and visitor registration modules.
Photo
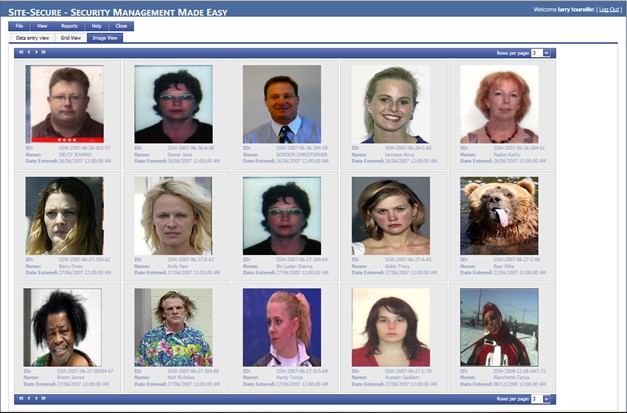
Access images of restricted people.
All features
Record individual names and any aliases
Assign restriction levels
Store the author’s name that entered the restriction
Store the source of each restriction
Access the image of the restricted person
Send emergency broadcast messages
Set expiry dates
Screenshots

FAQ
Yes. A restriction can have an expiry date to meet the requirements of a suspension or comply with a restraining order.
Yes. A special handling message can be customized and assigned to each individual.
Only authorized users can assign a restriction to a person. The user’s name will audited. The user may also be required to enter a PIN code to save the entry.
In most situations, an image will be entered into the system and used to validate the restricted person.
Testimonials



Newsletter