Key Management

So much more than key management
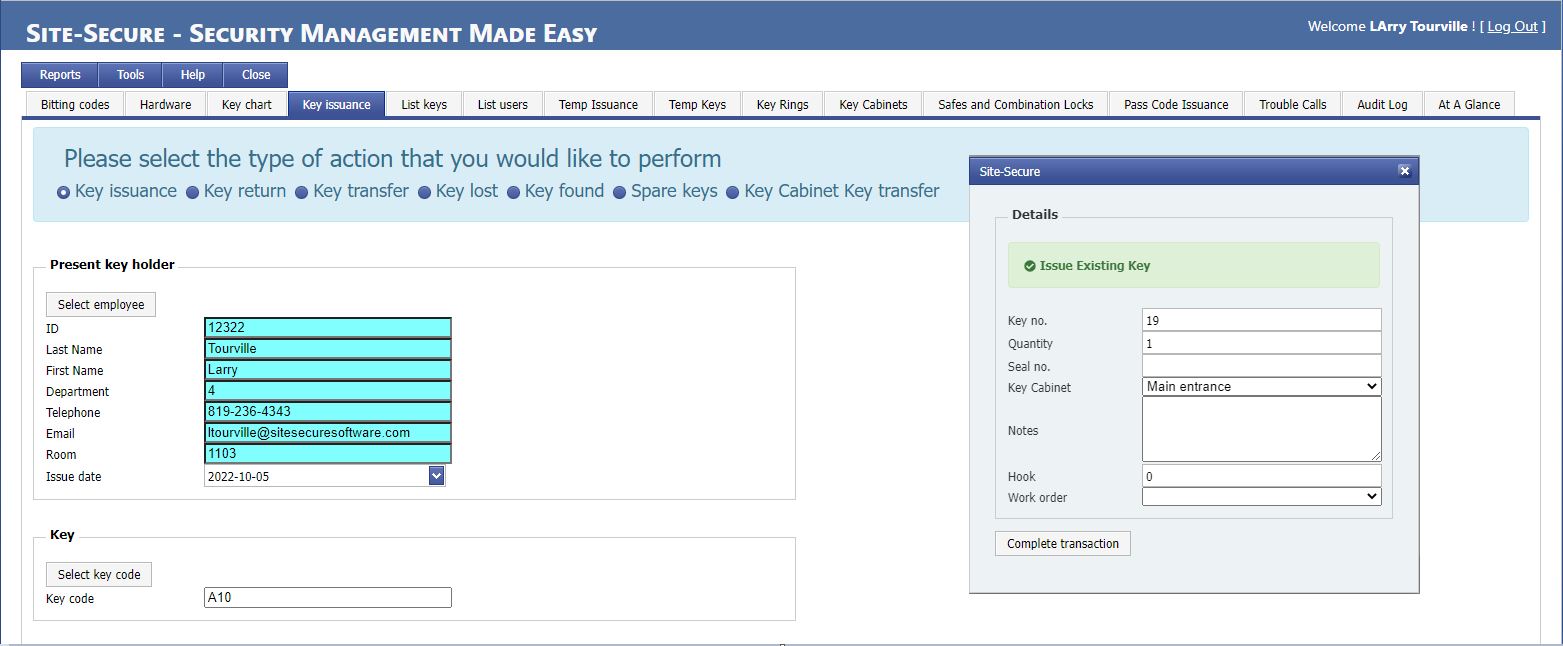
The key management module will greatly assist anyone who must manage a large key inventory system, safes and combination locks, cypher locks, and even alarm system passcodes. This module is used to accurately track key transfers, issuances, returns, replacements, etc. It includes such features as automatic information links for re-keying, identification of old keys to be returned by users as well as all the necessary information for key re-issuance. Lock cylinders can be removed and catalogued for later re-use. Biting codes can be encrypted for enhanced security.
Reduce costs through automation
Extensive information can be kept on each door type, including wooden/metal/glass door, single or double door, number and type of hinges, type of door closer, lock details, electric locks, electric hinges, card access controlled, alarm monitored, frame types, and grouted or hollow. This information can be invaluable to locksmiths, since they can properly prepare for the door repair, thereby reducing repair times. This module uses data from the personnel information management module to track who should have keys to which area, validate the authorization to issue keys, and the proof of identity required to receive keys.

Automatic email notifications can be sent for non returned keys, re-keying, and re-issuance of passcodes.
iForms requests
Forms based automated key requests and approval processes can be managed.
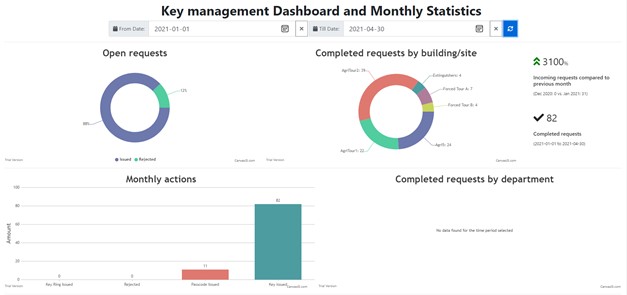
Dashboard
The visual dashboard displays the visitors in facility, attendance count by facility, monthly attendance statistics and previous monthly comparison.
Padlock or combination lock
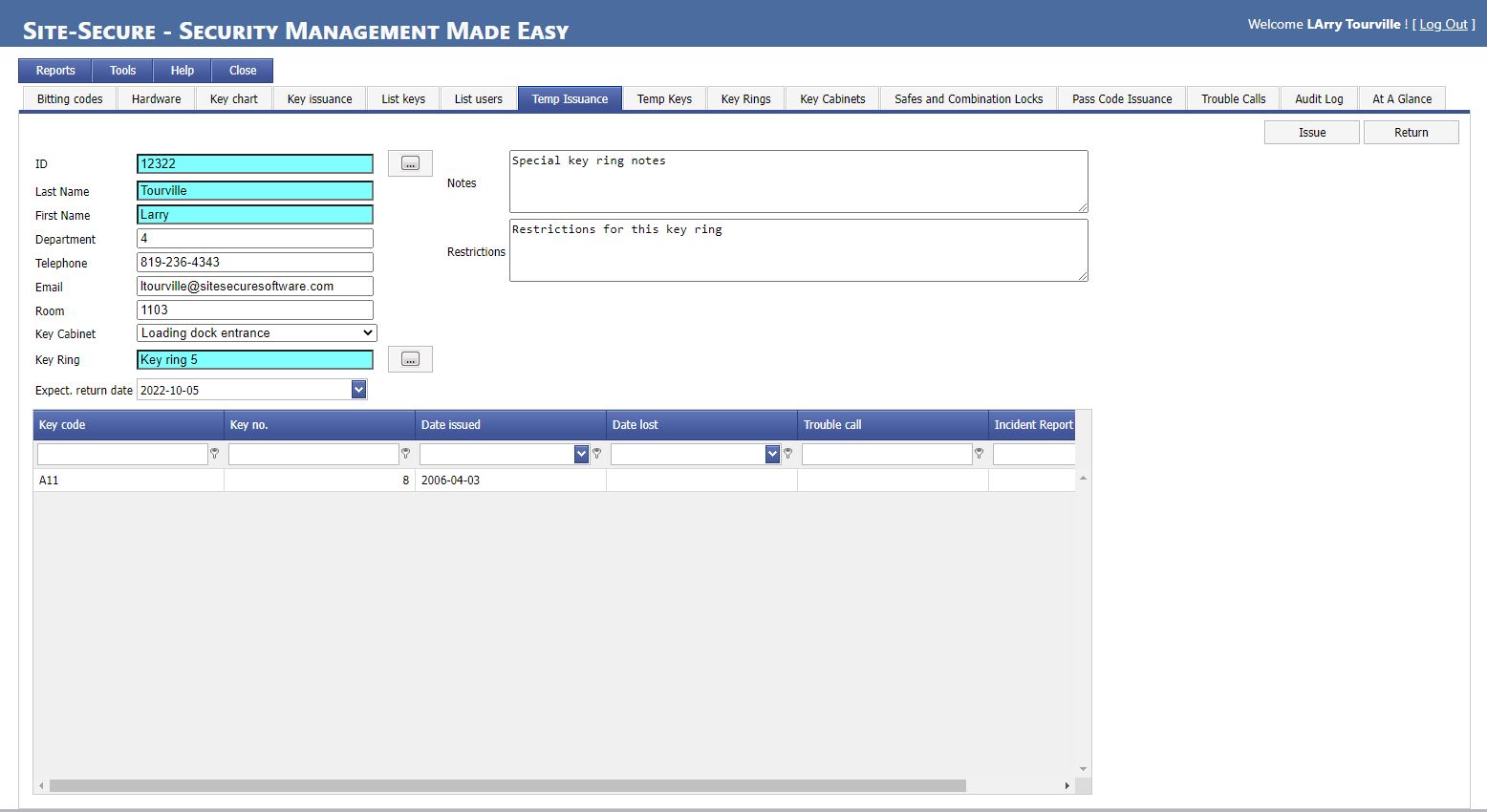
Special restrictions and instructions for key issuances can be configured.
All features
Automatic information for re-keying, key re-issuance, etc.
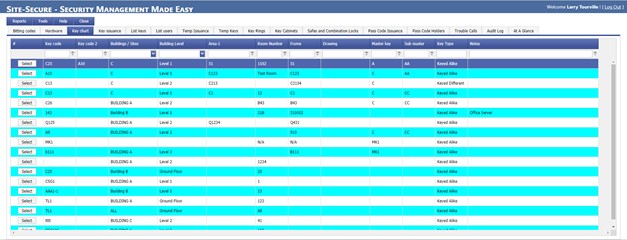
Multiple search capabilities by key codes master keys, code families
Automatic flags for restricted persons, requesting keys already received, etc.
Automatic flag if a requested key is in the cabinet displaying the hook number
Automatic key assignement numbers as keys are cut
Automatic updates of user files with dates of transaction
Automatic printing of key signature acceptance form
Manages all key biting codes
Tracking of number of copies issued and in stock for any given key
Comprehensive door hardware and inventory database
Tracking and reporting of key issuances and returns
Tracking and reporting of safes, cypher locks, combinations, alarm codes, etc.
Screenshots

FAQ
An automatic email is sent, advising of overdue return. An escalation process is also available.
Yes. Each system can be configured to adapt to the client’s environment.
Yes. In the default settings, most fields can be configured as visible/mandatory based on user requirements.
Yes. The system can be partionned to limit who can see/access reports.
Testimonials



Newsletter